CentOS Stream 9 can be configured to provide remote access to the graphical desktop environment over a network or internet connection. Although not enabled by default, displaying and accessing a CentOS 9 desktop from a system anywhere else on a network or the internet is relatively straightforward. This can be achieved regardless of whether that system runs Linux, Windows, or macOS. There are even apps available for Android and iOS that will allow you to access your CentOS 9 desktop from just about anywhere that a data signal is available.
Remote desktop access can be helpful in many scenarios. For example, it enables you or another person to view and interact with your CentOS 9 desktop environment from another computer system on the same network or over the internet. This is useful if you need to work on your computer when you are away from your desk, such as while traveling. It is also helpful when a coworker or IT support technician needs access to your desktop to resolve a problem.
When the CentOS 9 system runs on a cloud-based server, it also allows access to the desktop environment as an alternative to performing administrative tasks using the command-line prompt or Cockpit web console.
The CentOS 9 remote desktop functionality is based on a technology known as Virtual Network Computing (VNC). This chapter will cover the key aspects of configuring and using remote desktops within CentOS 9.
Secure and Insecure Remote Desktop Access
In this chapter, we will cover both secure and insecure remote desktop access methods. The insecure access method is generally safe if you access one system from another within a secure internal network. If, on the other hand, you plan to access your desktop remotely over any public network, you must use the secure method of access to avoid your system and data being compromised.
 |
You are reading a sample chapter from CentOS Stream 9 Essentials. Buy the full book now in eBook or Print format.
Full book includes 34 chapters and 290 pages. Learn more. |
Installing the GNOME Desktop Environment
It is, of course, only possible to access the desktop environment if the desktop itself has been installed. If, for example, the system was initially configured as a server, it is unlikely that the desktop packages were installed. The easiest way to install the packages necessary to run the GNOME desktop is to perform a group install. The key to installing groups of packages to enable a specific feature is knowing the group’s name. At the time of writing, there are two groups for installing the desktop environment on CentOS 9: “Server with GUI” and “Workstation”. As the group names tend to change from one CentOS 9 release to another, it is helpful to know that the list of groups that are either installed or available to be installed can be obtained using the dnf utility as follows:
# dnf grouplist
Available Environment Groups:
Server with GUI
Minimal Install
Workstation
Custom Operating System
Virtualization Host
Installed Environment Groups:
Server
Installed Groups:
Container Management
Headless Management
Available Groups:
Legacy UNIX Compatibility
Graphical Administration Tools
Smart Card Support
RPM Development Tools
.NET Development
System Tools
Development Tools
Console Internet Tools
Security Tools
Network Servers
Scientific SupportCode language: plaintext (plaintext)The Workstation environment group is listed as available (and therefore not already installed) in the above example. To find out more information about the contents of a group before installation, use the following command:
# dnf groupinfo workstation
Environment Group: Workstation
Description: Workstation is a user-friendly desktop system for laptops and PCs.
Mandatory Groups:
Common NetworkManager submodules
Core
Fonts
GNOME
Guest Desktop Agents
Hardware Support
Internet Browser
Multimedia
Printing Client
Standard
Workstation product core
base-x
Optional Groups:
Backup Client
GNOME Applications
Headless Management
Internet Applications
Office Suite and Productivity
Remote Desktop Clients
Smart Card SupportCode language: plaintext (plaintext)Having confirmed that this is the correct group, it can be installed as follows:
# dnf groupinstall workstationCode language: Shell Session (shell)Once installed, and assuming that the system has a display added, the desktop can be launched using the following startx command:
$ startxCode language: Shell Session (shell)To launch the graphical desktop each time the system starts, change the default target as follows:
 |
You are reading a sample chapter from CentOS Stream 9 Essentials. Buy the full book now in eBook or Print format.
Full book includes 34 chapters and 290 pages. Learn more. |
# systemctl set-default graphical.targetCode language: plaintext (plaintext)If, on the other hand, the system is a server with no directly connected display, the only way to run and access the desktop will be to configure VNC support on the system.
Installing VNC on CentOS Stream 9
Access to a remote desktop requires a VNC server installed on the remote system, a VNC viewer on the system from which access is being established, and, optionally, a secure SSH connection. While several VNC server and viewer implementations are available, Red Hat has standardized on TigerVNC, which provides both server and viewer components for Linux-based operating systems. VNC viewer clients for non-Linux platforms include RealVNC and TightVNC. To install the TigerVNC server package on CentOS 9, run the following command:
# dnf install tigervnc-serverCode language: Shell Session (shell)If required, the TigerVNC viewer may also be installed as follows:
# dnf install tigervncCode language: Shell Session (shell)Once the server has been installed, the system must be configured to run one or more VNC services and open the appropriate ports on the firewall.
Configuring the VNC Server
With the VNC server packages installed, the next step is configuring the server. The first step is to specify a password for the remote desktop environment user. While logged in as root, execute the vncpasswd command (where the user name is assumed to be demo):
 |
You are reading a sample chapter from CentOS Stream 9 Essentials. Buy the full book now in eBook or Print format.
Full book includes 34 chapters and 290 pages. Learn more. |
# su - demo
[demo@demoserver ~]$ vncpasswd
Password:
Verify:
Would you like to enter a view-only password (y/n)? n
A view-only password is not used
[demo@demoserver ~]$ exit
#Code language: plaintext (plaintext)Next, a VNC server configuration file named [email protected] must be created in the /etc/ systemd/system directory. The content of this file should read as follows, where all instances of <USER> are replaced with the username referenced when the VNC password was set:
[Unit]
Description=Remote desktop service (VNC)
After=syslog.target network.target
[Service]
Type=forking
WorkingDirectory=/home/<USER>
User=<USER>
Group=<USER>
ExecStartPre=/bin/sh -c '/usr/bin/vncserver -kill %i > /dev/null 2>&1 || :'
ExecStart=/usr/bin/vncserver -autokill %i
ExecStop=/usr/bin/vncserver -kill %i
Restart=on-success
RestartSec=15
[Install]
WantedBy=multi-user.targetCode language: plaintext (plaintext)Next, the firewall needs to be configured to provide external access to the VNC server for remote VNC viewer instances, for example:
# firewall-cmd --permanent --zone=public --add-port=5901/tcp
# firewall-cmd --reloadCode language: Shell Session (shell)With the service configuration file created, the service needs to be enabled and started as follows:
# systemctl daemon-reload
# systemctl start vncserver@:1.service
# systemctl enable vncserver@:1.serviceCode language: plaintext (plaintext)Note that :1 is included in the service name to indicate that this is the service for VNC server display number 1. This matches port 5901, which was previously opened in the firewall. Check that the service has started successfully as follows:
# systemctl status vncserver@:1.serviceCode language: plaintext (plaintext)If the service fails to start, run the journalctl command to check for error messages:
 |
You are reading a sample chapter from CentOS Stream 9 Essentials. Buy the full book now in eBook or Print format.
Full book includes 34 chapters and 290 pages. Learn more. |
# journalctl -xeCode language: plaintext (plaintext)Also, try again after rebooting the system. If the service continues to fail, the VNC server can be started manually by logging in as the designated user and running the vncserver command:
$ vncserver :1Code language: plaintext (plaintext)Connecting to a VNC Server
VNC viewer implementations are available for a wide range of operating systems. Therefore, a quick internet search will likely provide numerous links containing details on obtaining and installing this tool on your chosen platform.
From the desktop of a Linux system on which a VNC viewer such as TigerVNC is installed, a remote desktop connection can be established as follows from a Terminal window:
$ vncviewer <hostname>:<display number>Code language: plaintext (plaintext)In the above example, <hostname> is either the hostname or IP address of the remote system and <display number> is the display number of the VNC server desktop, for example:
$ vncviewer 192.168.1.115:1Code language: Shell Session (shell)Alternatively, run the command without any options to be prompted for the details of the remote server:
 |
You are reading a sample chapter from CentOS Stream 9 Essentials. Buy the full book now in eBook or Print format.
Full book includes 34 chapters and 290 pages. Learn more. |
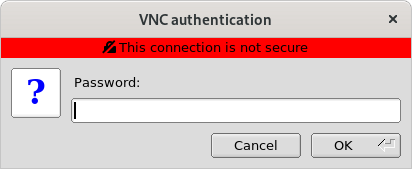
Enter the hostname or IP address followed by the display number (for example, 192.168.1.115:1) into the VNC server field and click on the Connect button. The viewer will prompt for the user’s VNC password to complete the connection, at which point a new window containing the remote desktop will appear.
This section assumed that the remote desktop was accessed from a Linux or UNIX system; the same steps apply to most other operating systems.
Connecting to a remote VNC server using the steps in this section results in an insecure, unencrypted connection between the client and server. This means the data transmitted during the remote session is vulnerable to interception. Therefore, a few extra steps are necessary to establish a secure and encrypted connection.
Establishing a Secure Remote Desktop Session
The remote desktop configurations explored in this chapter are considered insecure because no encryption is used. This is acceptable when the remote connection does not extend outside an internal network protected by a firewall. However, a more secure option is needed when a remote session is required over an internet connection. This is achieved by tunneling the remote desktop through a secure shell (SSH) connection. This section will cover how to do this on Linux, UNIX, and macOS client systems.
The SSH server is typically installed and activated by default on CentOS 9 systems. If this is not the case on your system, refer to the chapter Configuring SSH Key-based Authentication on CentOS Stream 9.
 |
You are reading a sample chapter from CentOS Stream 9 Essentials. Buy the full book now in eBook or Print format.
Full book includes 34 chapters and 290 pages. Learn more. |
Assuming the SSH server is installed and active, it is time to move to the other system. At the other system, log in to the remote system using the following command, which will establish the secure tunnel between the two systems:
$ ssh -l <username> -L 5901:localhost:5901 <remotehost>Code language: plaintext (plaintext)In the above example, <username> references the user account on the remote system for which VNC access has been configured, and <remotehost> is either the hostname or IP address of the remote system, for example:
$ ssh -l neilsmyth -L 5901:localhost:5901 192.168.1.115Code language: plaintext (plaintext)When prompted, log in using the account password. With the secure connection established, it is time to launch vncviewer to use the secure tunnel. Leaving the SSH session running in the other terminal window, launch another terminal and enter the following command:
$ vncviewer localhost:5901Code language: plaintext (plaintext)The vncviewer session will prompt for a password if one is required, and then launch the VNC viewer providing secure access to your desktop environment.
Although the connection is now secure and encrypted, the VNC viewer will most likely still report that the connection is insecure. Figure 16-2, for example, shows the warning dialog displayed by the RealVNC viewer running on a macOS system:
 |
You are reading a sample chapter from CentOS Stream 9 Essentials. Buy the full book now in eBook or Print format.
Full book includes 34 chapters and 290 pages. Learn more. |
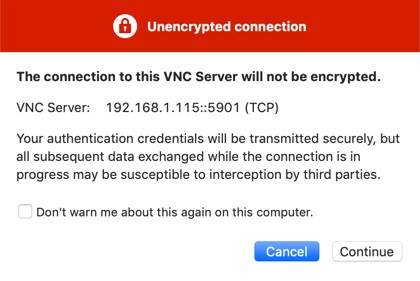
Unfortunately, although the connection is now secure, the VNC viewer software has no way of knowing this and consequently continues to issue warnings. However, rest assured that as long as the SSH tunnel is being used, the connection is indeed secure.
In the above example, we left the SSH tunnel session running in a terminal window. However, if you would prefer to run the session in the background, this can be achieved by using the –f and –N flags when initiating the connection:
$ ssh -l <username> -f -N -L 5901:localhost:5901 <remotehost>Code language: plaintext (plaintext)The above command will prompt for a password for the remote server and then establish the connection in the background, leaving the terminal window available for other tasks.
If you are connecting to the remote desktop from outside the firewall, keep in mind that the IP address for the SSH connection will be the external IP address provided by your ISP or cloud hosting provider, not the LAN IP address of the remote system (since this IP address is not visible to those outside the firewall). Therefore, you will also need to configure your firewall to forward port 22 (for the SSH connection) to the IP address of the system running the desktop. It is not necessary to forward port 5900. Steps to perform port forwarding differ between firewalls, so refer to the documentation for your firewall, router, or wireless base station for details specific to your configuration.
Establishing a Secure Tunnel on Windows using PuTTY
A similar approach is taken to establishing a secure desktop session from a Windows system to a CentOS Stream 9 server. Assuming you already have a VNC client such as TightVNC installed, the remaining requirement is a Windows SSH client (in this case, PuTTY).
 |
You are reading a sample chapter from CentOS Stream 9 Essentials. Buy the full book now in eBook or Print format.
Full book includes 34 chapters and 290 pages. Learn more. |
Once PuTTY is downloaded and installed, the first step is establishing a secure connection between the Windows system and the remote CentOS 9 system, configuring appropriate tunneling. When launched, PuTTY displays the following screen:
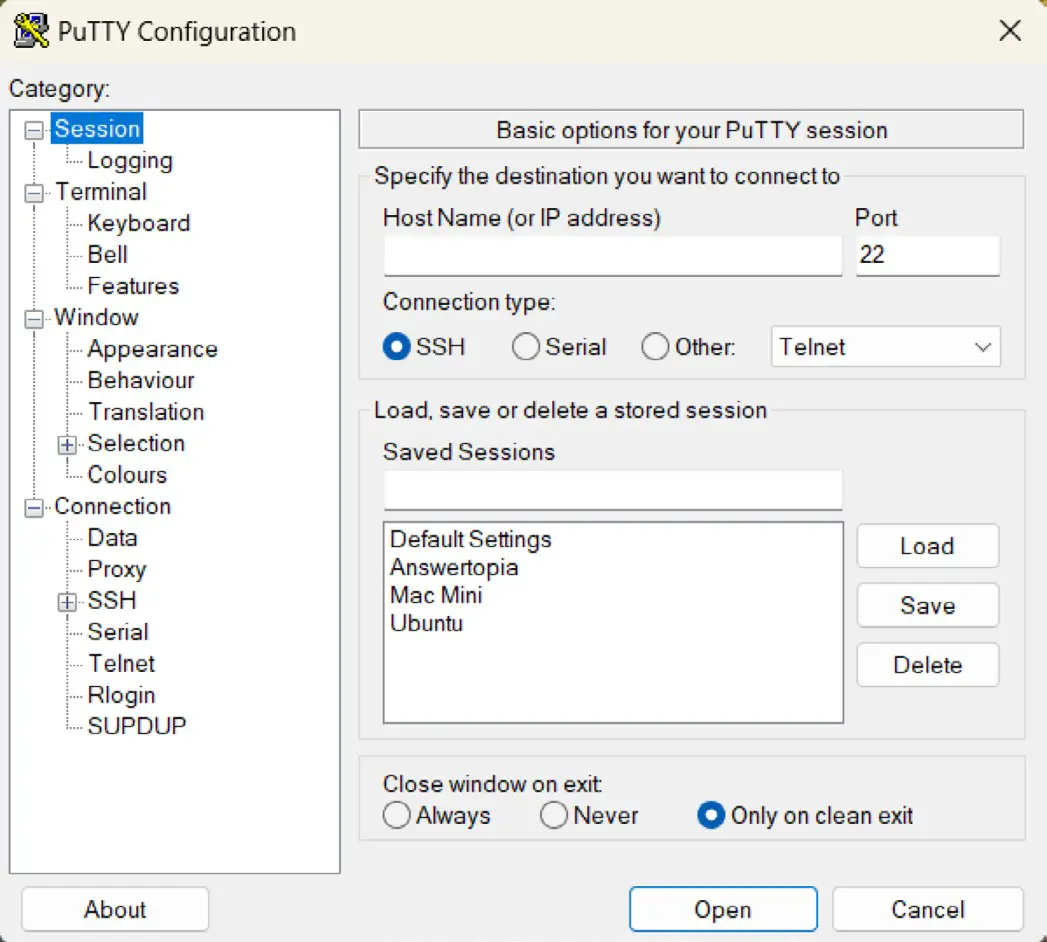
Enter the IP address or hostname of the remote host (or the external IP address of the gateway if you are connecting from outside the firewall). The next step is to set up the tunnel. Click on the + next to SSH in the Category tree on the left-hand side of the dialog and select Tunnels. The screen should subsequently appear as follows:
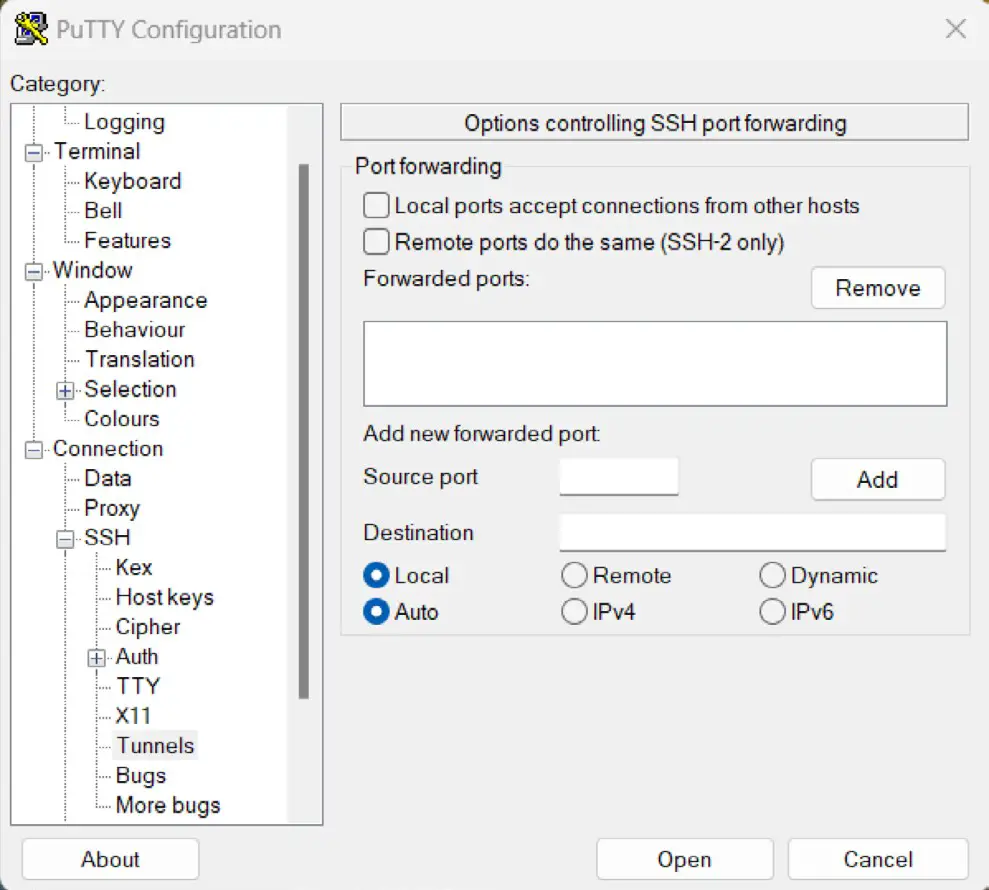
Enter 5901 as the Source port and localhost:5901 as the Destination, and click the Add button. Finally, return to the main screen by clicking on the Session category. Enter a name for the session in the Saved Sessions text field and press Save. Click on Open to establish the connection. A terminal window will appear with the login prompt from the remote system. Enter the appropriate user login and password credentials.
The SSH connection is now established. Launch the TightVNC viewer, enter localhost:5901 in the VNC Server text field, and click Connect. The viewer will establish the connection, prompt for the password, and then display the desktop. You are now accessing the remote desktop of a Linux system from Windows over a secure SSH tunnel connection.
Shutting Down a Desktop Session
To shut down a VNC Server hosted desktop session, use the –kill command-line option and the number of the desktop to be terminated. For example, to kill desktop :1:
 |
You are reading a sample chapter from CentOS Stream 9 Essentials. Buy the full book now in eBook or Print format.
Full book includes 34 chapters and 290 pages. Learn more. |
# vncserver –kill :1Code language: plaintext (plaintext)Troubleshooting a VNC Connection
With so much happening in the background, VNC can sometimes seem opaque, particularly when problems arise, and the server fails to start or connect, resulting in error messages. There are, however, some techniques for tracking down and resolving VNC problems:
If the VNC service fails to start, check the systemctl status of the service and check for error messages:
# systemctl status vncserver@:1.serviceCode language: plaintext (plaintext)For more detailed information, check the systemd journal by running the journalctl command:
# journalctl -xeCode language: Shell Session (shell)Additional information may be available in the log file located at:
/home/<username>/.vnc/<hostname>.<domain>:<display number>.log Code language: plaintext (plaintext)For example:
 |
You are reading a sample chapter from CentOS Stream 9 Essentials. Buy the full book now in eBook or Print format.
Full book includes 34 chapters and 290 pages. Learn more. |
/home/neilsmyth/.vnc/demoserver01.localdomain:1.logCode language: plaintext (plaintext)If the systemd VNC service is still unable to start the VNC server, try starting it manually using the following command:
# vncserver :<display number> Code language: plaintext (plaintext)For example:
# vncserver :1Code language: plaintext (plaintext)Check the output and log file for errors that may help identify the problem. Then, if the server starts successfully, try connecting again with a VNC viewer.
If the VNC server appears to be running but attempts to connect from a viewer fail, it may be worth checking that the correct firewall ports are open. Begin by identifying the default zone as follows:
# firewall-cmd --get-default-zone publicCode language: plaintext (plaintext)Having obtained the default zone, check that the necessary ports are open:
 |
You are reading a sample chapter from CentOS Stream 9 Essentials. Buy the full book now in eBook or Print format.
Full book includes 34 chapters and 290 pages. Learn more. |
# firewall-cmd --permanent --zone=public --list-ports
5901/tcp 5900/tcpCode language: plaintext (plaintext)If a port used by VNC is not open, add the port as follows:
# firewall-cmd --permanent --zone=public --add-port=<port number>/tcpCode language: plaintext (plaintext)Summary
Remote access to the GNOME desktop environment of a CentOS Stream 9 system can be enabled by using Virtual Network Computing (VNC). Comprising the VNC server running on the remote server and a corresponding client on the local host, VNC allows remote access to multiple desktop instances running on the server.
When the VNC connection is being used over a public connection, SSH tunneling is recommended to ensure that the communication between the client and server is encrypted and secure.
